Covert Web-to-App Tracking via Localhost on Android
created: June 3, 2025, 12:12 p.m. | updated: June 4, 2025, 1:14 p.m.
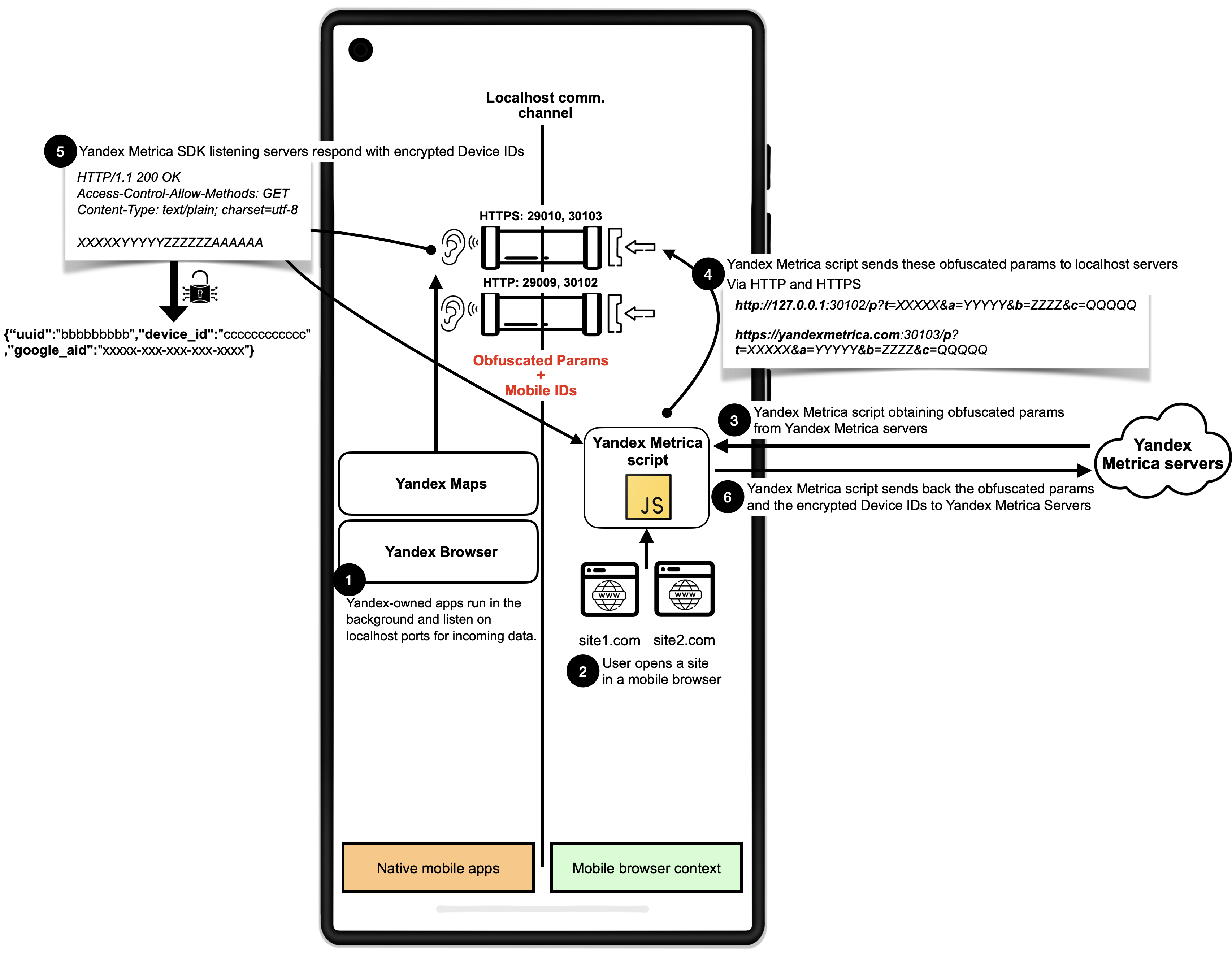
Yandex using localhost communications since 2017Yandex Metrica script initiates HTTP requests with long and opaque parameters to localhost through specific TCP ports: 29009, 29010, 30102, and 30103.
Our investigation revealed that Yandex-owned applications—such as Yandex Maps and Yandex Navigator, Yandex Search, and Yandex Browser— actively listen on these ports.
]com is resolving to the loopback address 127.0.0.1, and that the Yandex Metrica script transmits data via HTTPS to local ports 29010 and 30103.
As opposed to Meta's Pixel case, all this information is aggregated and uploaded together to the Yandex Metrica server (e.g., mc[.]yango[.
The Yandex Metrica script on the website receives these IDs and sends them to their servers alongside the obfuscated parameters.
6 months, 1 week ago: Hacker News